Baseline
Being the victim of a cyber attack can be scary, expensive, and potentially business-crippling.
So how do you prevent a cyber attack? Start with making security a priority for all IT operations, and the first place to start is by making systems as hacker proof as possible:
Gold Build Standard? Corporate Build or Hardened Build? Controlled Image? Baseline Configuration? You will find the need for a Gold Build Standard in all compliance frameworks (for example, NIST 800-53 CM-2 and CM-3, CIS Control 5.2, PCI DSS Requirement 2 and especially NERC CIP 007-3 and 010-3) as a means of guaranteeing security. Without a consistent build how else can you expect security to be maximized?
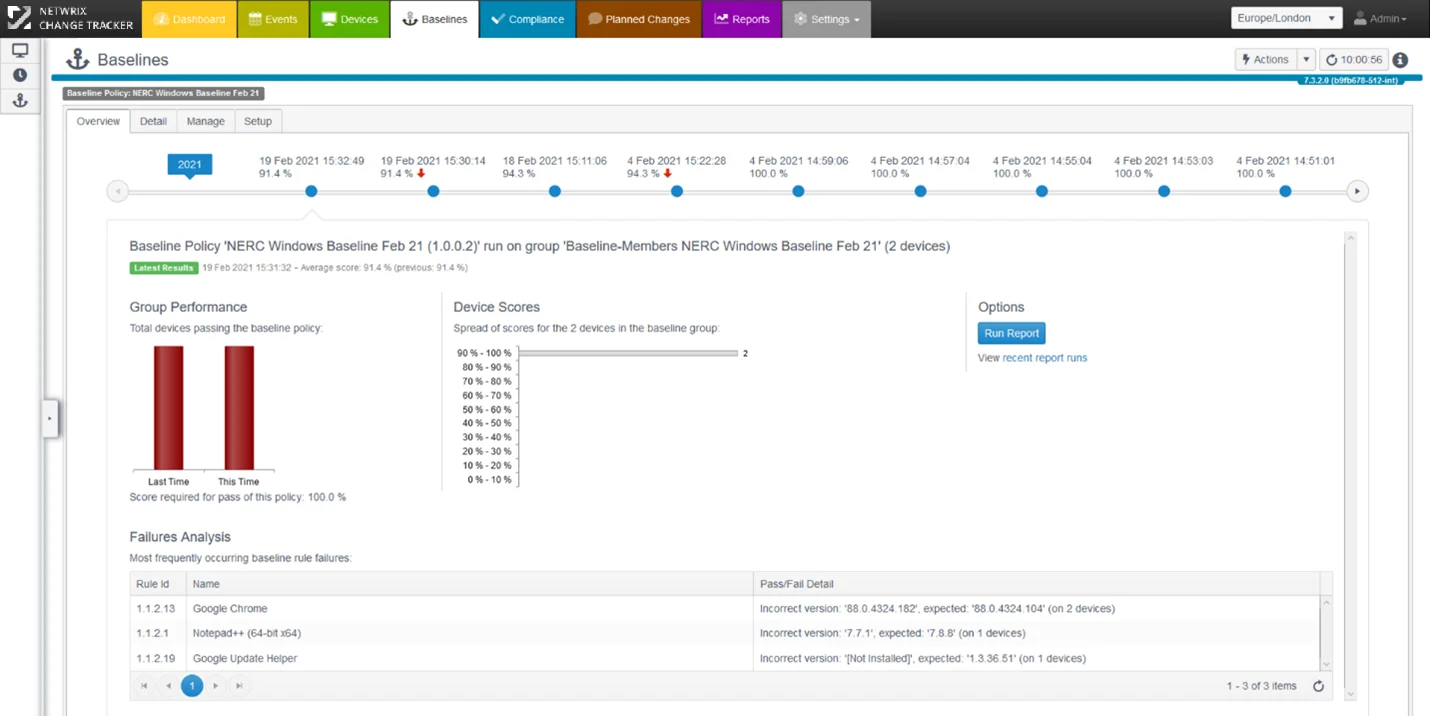
Change Tracker – Automated Development and Maintenance of a Configuration Baseline
Netwrix make the entire process of creating a Hardened Build Standard, then baselining and tracking configuration drift a 'Business as Usual' process.
In addition to an unlimited supply of published hardened build standards, such as the Center for Internet Security (CIS) Benchmarks or the DISA Security Technical Information Guides (STIG), now with Netwrix Change Tracker, any device can be used as a 'Baseline Source' and the specific configuration attributes required for your Baseline can be captured to create your own Gold Build Standard blueprint.
A simple Wizard UI walks you through the process so anyone can be building their own personalized baseline configuration and comparing other devices within a few minutes.