Enabling Deep Packet Inspection and Intercepting VPN Traffic on macOS Clients
Overview
This article describes how to enable Deep Packet Inspection and intercept VPN traffic on macOS clients. These instructions apply to Netwrix Endpoint Protector Server version 5.3.0.5 and later, and Netwrix Endpoint Protector Client version 2.2.1.5 and later. Ensure that you have installed the Netwrix Endpoint Protector Client and created the desired Content Aware Policy before proceeding.
Instructions
-
Open the Netwrix Endpoint Protector Server interface. In the Device Control section, select User, Computer, Group, or Global Settings. Click Manage Settings, then select Netwrix Endpoint Protector Client and enable Deep Packet Inspection.
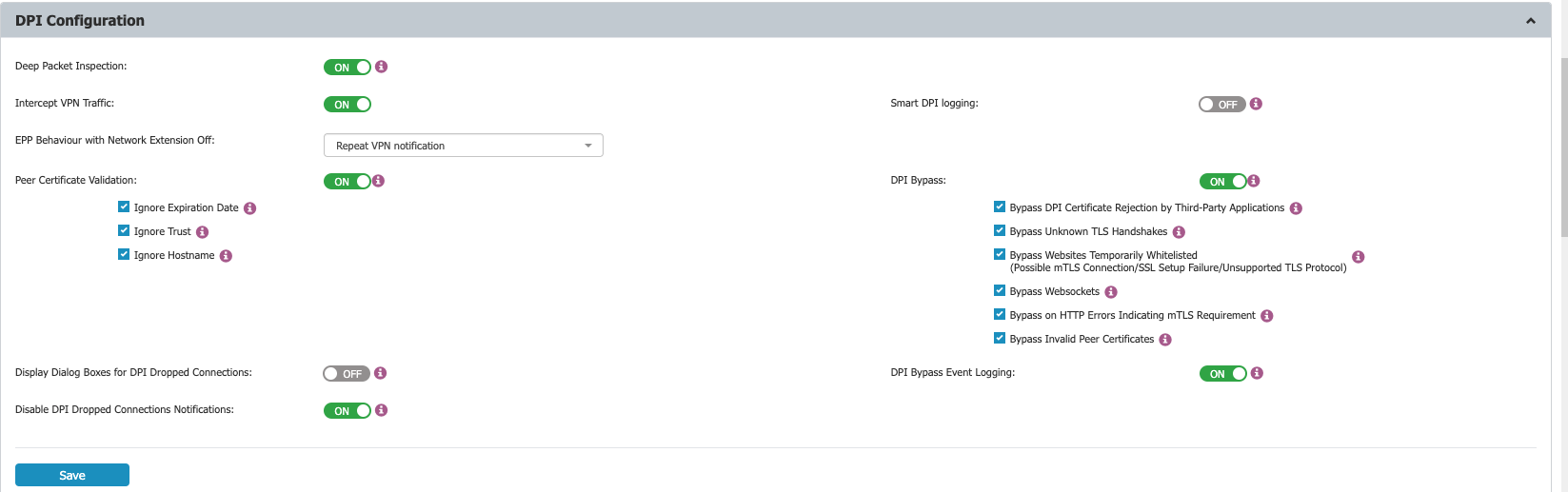
-
Navigate to System Configuration > System Settings > Deep Packet Inspection Certificate. Download the CA certificate.
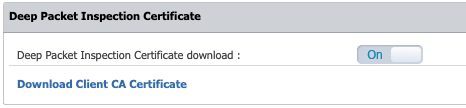
-
Open the Keychain Access application on your macOS device. In the sidebar, select System.
-
Extract the contents of the downloaded
ClientCertsfile. -
Locate the
cacert.pemfile. Drag and drop it into Keychain Access under System. -
Find the newly added certificate, which displays an “x” icon. Double-click the certificate.
-
In the Trust section, set When using this certificate to Always Trust.
-
Click Save to apply your changes.
-
In the Netwrix Endpoint Protector interface, enable Intercept VPN Traffic. When prompted, select one of the following behaviors for when the network extension is disabled:
- Temporary Disable Deep Packet Inspection: Temporarily disables Deep Packet Inspection.
- Block Internet Access: Blocks Internet access until the user approves the Netwrix Endpoint Protector Proxy Configuration. The user can allow it after restarting the computer.
- Repeat VPN Notification: Will repeat the network extension notification so that it can be allowed by the user. (This requires user interaction.)
-
Click Save to confirm your settings.
-
When prompted, review the pop-up message indicating that a system extension is blocked and must be allowed.
-
Open System Preferences, then navigate to Security and Privacy > General and allow the Netwrix Endpoint Protector Client extension.
-
When prompted, approve the Netwrix Endpoint Protector Proxy Configuration.
-
Confirm that Intercept VPN Traffic is enabled.
-
Disconnect and reconnect to the VPN to ensure all settings take effect in the Netwrix Endpoint Protector Client.