Action Types
The following tables list all available actions that can be added to an activity.
Pre-Session (Grant) Actions
| Action Type | Action Description | Related Fields |
|---|---|---|
| Add ADUC Permissions | Add AD rights to the login account | - AD Object Type — Select which type of object to manage in the Organizational Unit, a User or Computer. - AD Organizational Unit — Enter a pre-existing Organizational Unit the login account will have delegated permissions for. - AD Rights to be Added — Select which right will be delegated to the login account for managing the previously specified Organizational Unit - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add Microsoft Entra ID Role | Add login account to an Microsoft Entra ID role | - Microsoft Entra ID Role (Allows Custom Entries) — Enter which Microsoft Entra ID Directory Role will be added to the login account, or select from the Role options in the dropdown. - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add Sudoers Rule | Create a new rule file in sudoers.d directory to grant user additional permissions | - Run As — Enter which account(s) the logged-in user can run commands as - Commands — Enter which commands the user can run as a comma-separated list, or enter "ALL" for all commands on the target resource - Prompt for Password — If enabled, the logged-in user will need to enter their password to run elevated commands - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add to Microsoft Entra ID Group | Add login account to a Microsoft Entra ID Security Group | - Microsoft Entra ID Security Group (Allows Custom Entries) — Enter which Microsoft Entra ID Security Group will be added to the login account - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add User to Domain Group | Add login account to a domain group | - Domain — Enter an Active Directory domain - Group (Allows Custom Entries) — Enter a pre-existing Group the login account will be added to in the specified Domain - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add User to Local Group | Add login account to a local group | - Group (Allows Custom Entries) — Enter a pre-existing Group the login account will be added to in the specified Domain - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add Requester to Database Server | Add login account to the database server | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Add User to Database Role | Add login account the Database Role. | - Database – (Optional) If a database is specified, the role gets applied to the specific database. If the database field is left blank, the role gets applied to the database instance. - Role – The user is added to this role - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Create Windows File Share | Creates a temporary, encrypted SMB share on the activity's target Windows resource. This action creates a hidden lock file at the root of the share's map path. This is used by the console to identify a folder as being created/owned by the console. Users should not attempt to modify or delete this lock file. | - Windows File Share Name — The name of the File Share that will be created on the activity's target Windows resource - Windows File Share Map Path — A folder will be created in this location (local path) as a map for the session's Windows File Share - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Enable RDP on Host | Allows the user to enable RDP on the Host during the pre-session. This action comes paired with the Disable RDP on Host post-session action type. | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Monitor File for Changes | Monitors the specified file for modifications. If no changes are detected, an Info event is logged to the action log. If changes are detected (or the file goes missing after the pre-session hash), a Warning is logged to the action and event logs. | - File to Monitor — Enter the full local path to the file to be monitored - Fail Pre-Session on Missing File — Fail session provisioning if the file to monitor cannot be found - Fail Post-Session on Mismatch — Fail session during Activity post-session if monitored file checksum does not match - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Purge Kerberos Tickets for Host | Purge all Kerberos tickets from the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Purge Kerberos Tickets for User | Purge Kerberos Tickets for the login account | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run AD Replication for User | Runs AD replication for the target user within the AD site of the target resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run Custom PowerShell Script | Execute custom PowerShell script during Activity | - Definition — Enter a custom Powershell script here - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run Replication | Run replication (via repadmin /syncall) on closest domain controller to the target resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Scan Host for Local Groups | Scan local groups on the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Set Cisco User Privilege | Set Cisco user Privilege level for account access (1-15) 1 = lowest rights 15 = highest rights | - Privilege — User Privilege level for account access (1-15) 1 = lowest rights 15 = highest rights - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
Session (Connect) Actions
| Action Type | Action Description | Related Fields |
|---|---|---|
| Monitor for User Log in | Monitor the target resource for a login by the user | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Purge Kerberos Tickets for Host | Purge all Kerberos tickets from the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Purge Kerberos Tickets for User | Purge Kerberos Tickets for the login account | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run Custom PowerShell Script | Execute custom PowerShell script during Activity | - Definition — Enter a custom Powershell script here - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run Replication | Run replication (via repadmin /syncall) on closest domain controller to the target resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Scan Host for Local Groups | Scan local groups on the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
Post-Session (Remove) Actions
| Action Type | Action Description | Related Fields |
|---|---|---|
| Disable RDP on Host | Disable RDP on target resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Invoke Protection Policy | Validate membership of protected groups and remove unauthorized accounts | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Logoff User | Log user off on Activity session close | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Monitor File for Changes | Monitors the specified file for modifications. If no changes are detected, an Info event is logged to the action log. If changes are detected (or the file goes missing after the pre-session hash), a Warning is logged to the action and event logs. | - File to Monitor — Enter the full local path to the file to be monitored - Fail Pre-Session on Missing File — Fail session provisioning if the file to monitor cannot be found - Fail Post-Session on Mismatch — Fail session during Activity post-session if monitored file checksum does not match - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Purge Kerberos Tickets for Host | Purge all Kerberos tickets from the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Purge Kerberos Tickets for User | Purge Kerberos Tickets for the login account | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Remove ADUC Permission | Remove AD rights from the login account | - AD Object Type — Select which type of object to manage in the Organizational Unit, a User or Computer. - AD Organizational Unit — Enter a pre-existing Organizational Unit the login account will have delegated permissions for. - AD Rights to be Added — Select which right will be delegated to the login account for managing the previously specified Organizational Unit - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove from Microsoft Entra ID Role | Remove Microsoft Entra ID role from the login account | - Microsoft Entra ID Role (Allows Custom Entries) — Enter which Microsoft Entra ID Directory Role will be added to the login account, or select from the Role options in the dropdown. - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove Requester from Database Server | Remove the login user from the database | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove User from Database Role | Remove the "Remove User from Database Role" login user from the given database role | - Database – (Optional) If a database is specified, the role gets removed from the specific database. If the database field is left blank, the role gets removed from the login user in the database instance. - Role – The user is removed from this role - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove Sudoers rule | Remove previously created file in Sudoers directory | - Run As — Enter which account(s) the logged-in user can run commands as - Commands — Enter which commands the user can run as a comma-separated list, or enter "ALL" for all commands on the target resource - Prompt for Password — If enabled, the logged-in user will need to enter their password to run elevated commands - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove User from Domain Group | Remove login account from domain group | - Domain — Enter an Active Directory domain - Group (Allows Custom Entries) — Enter a pre-existing Group the login account will be added to in the specified Domain - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Remove User from Local Group | Remove login account from local group | - Group (Allows Custom Entries) — Enter a pre-existing Group the login account will be added to in the specified Domain - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action - Paired Action's Name — (Optional) Edit the name of the paired action |
| Run Custom PowerShell Script | Execute custom PowerShell script during Activity | - Definition — Enter a custom Powershell script here - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Run Replication | Run replication (via repadmin /syncall) on closest domain controller to the target resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Scan Host for Local Groups | Scan local groups on the resource | - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
| Set Cisco User Privilege | Set Cisco user Privilege level for account access (1-15) 1 = lowest rights 15 = highest rights | - Privilege — User Privilege level for account access (1-15) 1 = lowest rights 15 = highest rights - Continue on Error — If an error occurs, continue to the next step rather than halting the action - Action Name — (Optional) Edit the name of the action |
Add Action Window
The Add Action window varies slightly based on the Action Type selected and the associated session part. Follow the instructions to add actions to the activity.
Step 1 – Navigate to the Activities page.
Step 2 – In the Activities list, select the name of an activity.
Step 3 – In the Actions section, for each of the following, click the Add icon.
- Pre-Session (Grant) — List of actions that will run before the session begins. These actions may be paired with a corresponding Post-Session action.
- Session (Connect) — List of actions that will run during the session
- Post-Session (Remove) — List of actions that will run after the session completes.
These actions may be paired with a corresponding Pre-Session action.
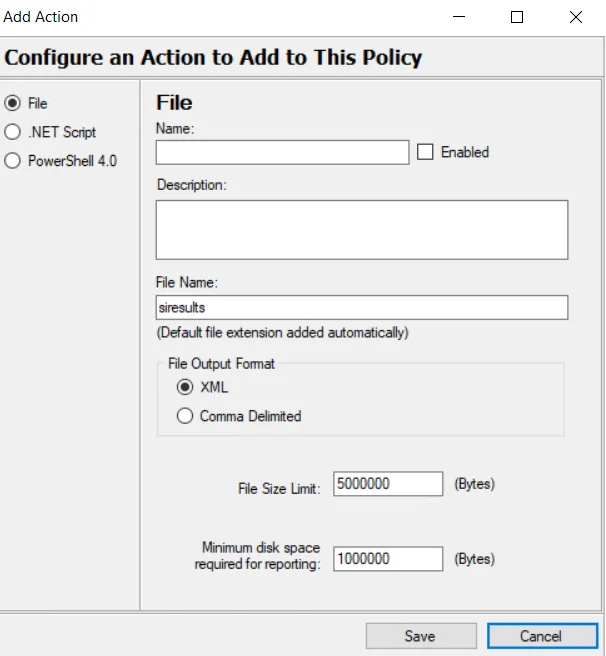
Step 4 – Complete the following fields:
- Action Type - Icon indicates the type of object.
- AD Object Type - AD Object Type — Select which type of object to manage in the Organizational Unit, a User or Computer..
- AD Organizational Unit for the Action - AD Organizational Unit — Enter a pre-existing Organizational Unit the login account will have delegated permissions for.
- AD Rights to be Added - AD Rights to be Added — Select which right will be delegated to the login account for managing the previously specified Organizational Unit.
- Continue on Error - Continue on Error — If an error occurs, continue to the next step rather than halting the action.
- Action Name - Action Name — (Optional) Edit the name of the action.
- Paired Actions Name - Paired Action's Name — (Optional) Edit the name of the paired action
See the Action Types section for detailed descriptions of the fields.
NOTE: The fields will change depending on the selected Action Type.
Step 5 – Click Okay to create the new action.
Step 6 – Continue to create as many actions for each stage of the session (Grant, Connect, Remove) as required.
NOTE: It is not possible to change the Action Type once the action is created. Delete the existing action and then create a new action to get a new Action Type.
Step 7 – If desired, it is possible to automatically run any Protection Policies associated with the resource when the session completes. Simply add the Invoke Protection Policies action to the Post-Session group. See the Protection Policies Page topic for additional information.
NOTE: It is not necessary to select a protection policy. All protection policies that apply to the session host are executed.
The new actions are added to the activity.