Manual Agent Deployment
The Threat PreventionAgent must be installed to the appropriate systems for monitoring. See the Agent Information topic for specifics on where to deploy.
The Threat Prevention Agent can be deployed through any of the following methods:
-
Deploy the Agent to server(s) through the Administration Console – You can deploy the Agent to one or multiple servers through the Administration Console
infoThis is the recommended method for deploying the Agent.
-
Manually through the Windows Agent Setup Wizard – Run the Agent executable to launch this wizard
See the Agents Interface topic and the Deploy Agents topic for additional information to deploy the Agent through the Administration Console.
Follow the steps to manually deploy the Agent.
Manually deploying the Agent requires an Enrollment Secret, which is a limited-life (1 hour) password generated by the Enterprise Manager. The Agent Installer uses it to ensure that the Agent is connected to a legitimate Enterprise Manager. Prior to launching the Threat Prevention Windows Agent Setup wizard, note the values for the enrollment secret and the EM certificate. See the Enrollment Secret Configuration Window topic for additional information.
Step 1 – From the Threat Prevention server, copy the Agent executable (
...\Netwrix\Netwrix Threat Prevention\SIEnterpriseManager\Setup\SI Agent.exe) to the machine where
you want to install the Agent. Then run the executable. The Netwrix Threat Prevention Windows Agent
Setup wizard opens.
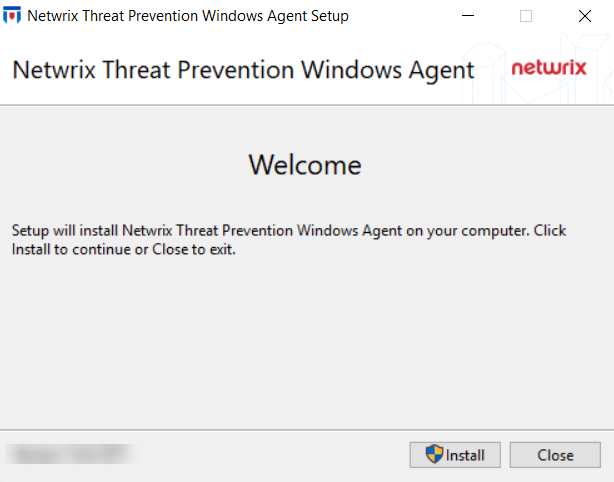
Step 2 – On the Welcome page, click Install. The Setup Progress page is displayed, followed by another Welcome page.

Step 3 – Click Next.
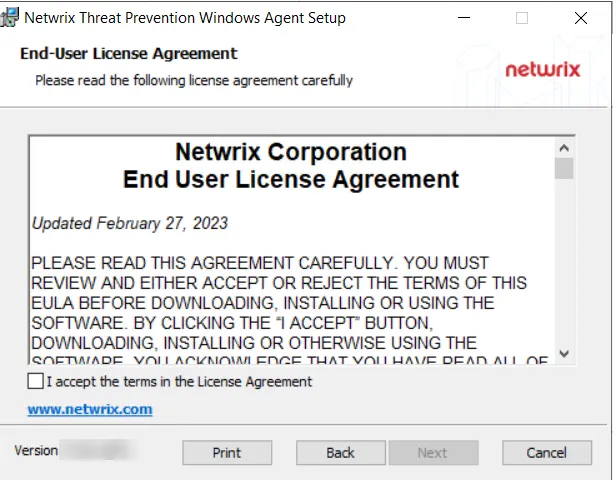
Step 4 – On the End-User License Agreement page, check the I accept the terms in the License Agreement box and click Next.
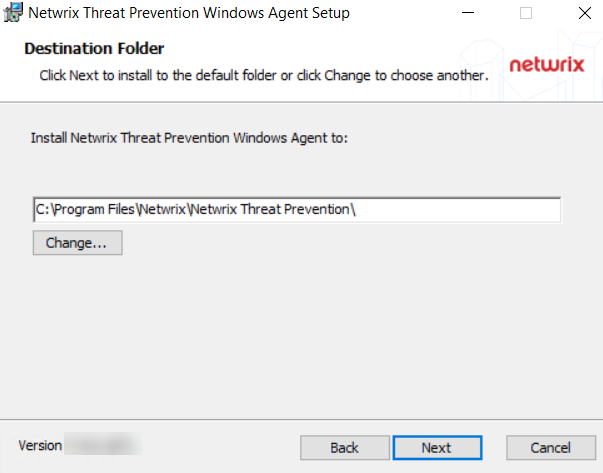
Step 5 – (Optional) On the Destination Folder page, change the installation directory location.
- To change the default installation directory location, click Change….
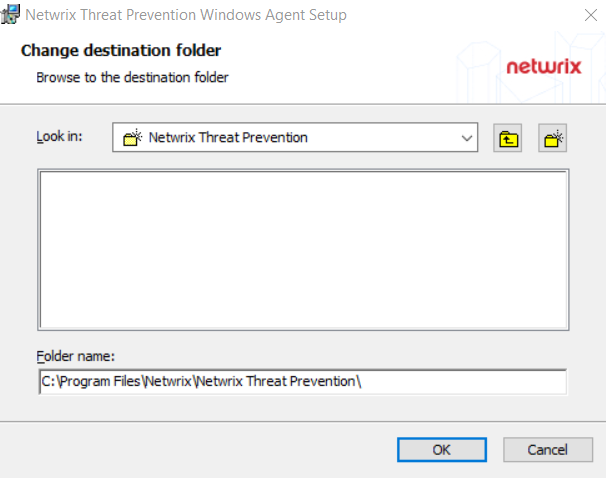
- Use the Look In field to select the desired installation folder.
- When the Folder name is as desired, click OK. The wizard returns to the Destination Folder page.
- Click Next.
To use the default installation directory location, skip the previous step and click Next on the Destination Folder page.
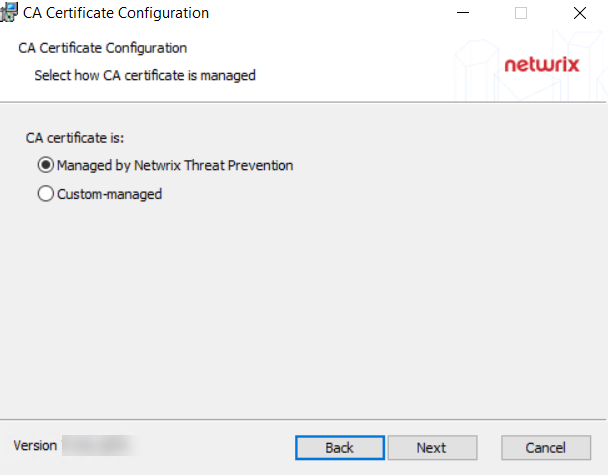
Step 6 – On the CA Certificate Configuration page, select one of the following options for the certificate and click Next:
- Managed by Netwrix Threat Prevention – To use certificates that are signed and managed by Threat Prevention
- Custom-managed – To use certificates that are signed by the customer's external certificate authority
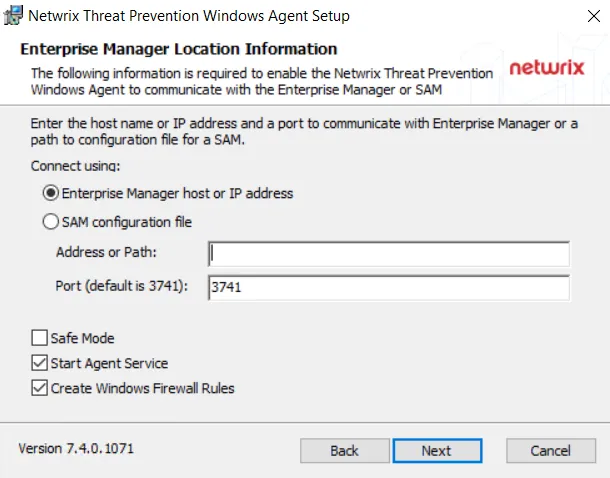
Step 7 – On the Enterprise Manager Location Information page, select the Option button for a product to enable communication with it.
-
Enterprise Manager host or IP address – For Threat Prevention
-
SAM configuration file – For Activity Monitor
-
In the Address or Path box, enter the following:
-
For Threat Prevention – Enter the host name or IP address of the machine where the Enterprise Manager service is located
-
For Activity Monitor – Enter the path to the activity agent configuration file for this host.
tipRemember, the Activity Monitor activity agent must already be deployed on the domain controller and enabled before installing the AD agent. The default path is:
…\Netwrix\Netwrix Threat Prevention\SIWindowsAgent\SAMConfig.xml
noteAs a requirement for using custom managed certificates, you must provide the Enterprise Manager server DNS name, hostname, or FQDN (instead of the IP address) when installing the following:
- Threat Prevention server
- Remote instance of the Administration Console
- Agent
See the Administration Console and Agent Not Communicating with the Enterprise Manager topics for additional information.
-
-
The default Enterprise Manager port is 3741. Modify if necessary. The port configuration only applies to the Enterprise Manager Host option.
noteOn selecting the Enterprise Manger host or IP address option button and providing valid information for the Enterprise Manager in the Address or Path and Port boxes, the Agent automatically connects to the Enterprise Manager.
-
Configure additional Agent options as desired:
-
Safe Mode – This option prevents the Windows AD Events monitoring module from loading if the LSASS DLL versions has been modified since the last time the Threat Prevention Windows Agent service was started.
-
Start Agent Service – This option starts the Threat Prevention Windows Agent service after the Agent is installed. If the Threat Prevention Windows Agent service is not started during installation, the Agent requires a manual start or needs to be started automatically after a server reboot. Until the Agent is started, no activity monitoring or blocking occurs.
noteIf Custom-managed is selected on the CA Certificate Configuration page, the Start Agent Service checkbox is disabled because Agent installer does not obtain a signed certificate from Enterprise Manager in the custom-managed mode. After installing the Agent, you must create and provide certificates signed by your certificate authority.
-
Create Windows Firewall Rules – This option creates the rules needed to open this port during the installation process. If using a third party firewall, uncheck this option and manually create the necessary firewall rules.
-
When the settings are configured, click Next.
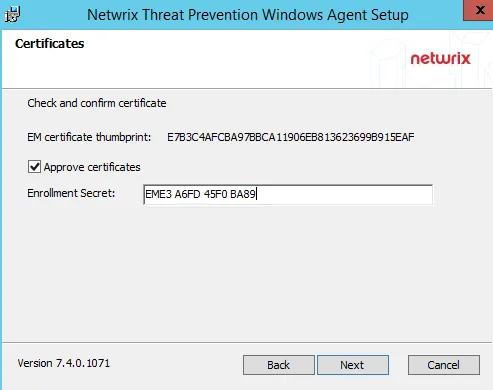
Step 8 – On the Certificates page, confirm the EM certificate hash by verifying that it contains the same value displayed in the Enrollment Secret Configuration Window in the Administration Console.
This page is not displayed when "Custom-managed" is selected on the CA Certificate Configuration wizard page .It is also not displayed when the Agent is reinstalled on a machine and the Certsinfo folder was not manually deleted, in which case the original certificates are re-used. The Certsinfo folder is located at: …\Netwrix\Netwrix Threat Prevention\SIWindowsAgent\CertsInfo\
-
Approve certificates – Select this checkbox to approve the thumbprint, which will then enable the Enrollment Secret box. Enter the enrollment secret obtained from the Enrollment Secret Configuration Window.
noteIf the enrollment secret has expired, you can generate a new one.
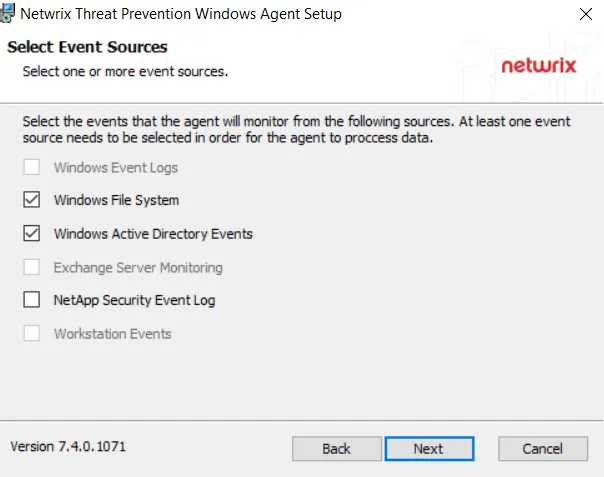
Step 9 – On the Select Event Sources page, select the types of events to be monitored by this Agent. The installer grays out options that are not applicable to the server where the Agent is being deployed. Click Next.
- Windows Event Logs – Available for legacy versions. Option should be grayed-out.
- Windows File System – Available as part of the Threat Prevention for File System and the Threat
Prevention for Active Directory solutions.
- Check this option if the system on which the Agent is being installed will be used for monitoring the local Windows file system
- Check this option if the system on which the Agent is being installed is a domain controller where Group Policy Object monitoring or blocking will be conducted
- Windows Active Directory Events – Available as part of the Threat Prevention for Active Directory
and the Threat Prevention for Exchange solutions. Also available as part of the Activity Monitor
for Active Directory solution.
- Select this component if the system the Agent is being installed on is an Active Directory domain controller. This option is grayed-out if the target system is not a domain controller.
- Exchange Server Monitoring – Available as part of the Threat Prevention for Exchange solution.
- Select this component if the system where the Agent is being installed is running the Exchange Server. This option will be grayed-out if this Agent is not being installed on an Exchange Server.
- NetApp Security Event Log – Available for legacy versions. Option should be grayed-out.
- Workstation Events – Available for legacy versions. Option should be grayed-out.
Step 10 – On the Ready to install Threat Prevention Windows Agent page, click Install. The Setup wizard displays the installation status. When the installation completes, the Operation Successful page is displayed.
Step 11 – When installation is complete, click Close.
If the certificates are managed by Threat Prevention, Agent deployment is completed. If the custom-managed certificate option was selected, see the Create Custom Managed Certificates for Each Agent topic for additional information.